Don’t Let Cost or Security Concerns Slow Down Your Cloud Journey
In this article, Media Temple examines why cloud costs and security are legitimate concerns, but also why they should not be constraints to public cloud adoption, especially since there are best practices and tools to mitigate the risks.
Cloud Security 101
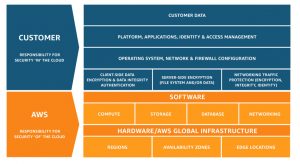
When it comes to security, all of the hyperscale public cloud providers work according to a shared responsibility model. Although there are slight differences from provider to provider, the AWS infographic below pretty much sums up the customer-provider division of responsibilities in the IaaS model. When it comes to PaaS and SaaS models, the boundary changes accordingly (with more responsibility shifting to the provider).
Many domains that handle sensitive personal data, such as healthcare, finance, and HR, to name but a few, are subject to strict regulatory requirements regarding the protection of cloud-based data from loss or unauthorized access—both at rest and in transit. In general, the European Union’s General Data Protection Regulation (GDPR), which came into effect in May 2018, has set a new global benchmark by giving EU citizens powerful rights over how their personal data is collected, stored, and processed. While cloud providers have invested heavily in GDPR and domain-specific compliance certifications, the ultimate responsibility and liability still lies squarely with the data owners and processors.
So, there is a lot at stake in ensuring that an organization’s cloud-based assets are secure, and there are various cloud characteristics that might make it harder to detect and deal with security vulnerabilities (versus with on-prem infrastructures). In particular, it can be hard to effectively monitor the complex multi-cloud and hybrid infrastructures that are favored by organizations today (84% and ~60% respectively, according to the 2019 RightScale report cited above).
Cloud Security Best Practices
In the belief that knowledge is power, the first step in mitigating potential cloud security risks is to understand them thoroughly as they apply to your organization, which includes clearly mapping the boundaries of your organization’s responsibilities in the shared provider-customer model. With that knowledge in hand, here are some best practices that allow you to reap the benefits of the cloud without compromising security:
- Design and enforce a robust data governance strategy so that you know at all times what data assets you have in the cloud and where, what their level of sensitivity is, which compliance regulations may apply to them, and which roles have legitimate reasons for accessing them.
- Implement strict access and authentication controls that can be applied consistently across your entire infrastructure.
- Traditional perimeter-based security measures implemented by a central operations or network team simply do not work in highly distributed and dynamic cloud environments. Security must become central to all development and IT operations in what is often called a “shift left” approach, whereby security is embedded at every stage of the application lifecycle, from design through continuous deployment.
- Although cloud skills gaps are becoming less and less of a challenge, cloud security practices and technologies are evolving at a rapid pace. You need to continually invest in the security knowledge and skills of your cloud team. It is also important to keep the entire organization abreast of cloud security risks and the role that each person and line of business can play in maintaining a high security profile.
- Despite all the measures and controls that you put in place, you may still experience a cloud security breach that leads to the exfiltration, corruption, or loss of data; and may also disrupt the end-user experience. Best practices that can minimize the direct and indirect costs of breaches include:
- Making sure that your cloud provider encrypts data at rest and that you have activated the option of in-transit encryption for your sensitive data.
- Implement frequent backups and replicate sensitive datasets across different geographic locations.
- Develop, implement, and regularly test a disaster recovery (DR) plan that minimizes both data loss (RPO) and downtime (RTO).
Cloud Security Stack
You are not alone in your efforts to secure your public cloud assets. The cloud providers themselves, as well as a whole slew of third-party vendors, have developed tools, services, and platforms to support access control and authentication, detect and prioritize threats, manage security events, orchestrate and automate cloud security workflows, and prevent data exfiltration. A few selected examples are AWS Identity and Access Management (IAM), Fortinet, Symantec, and next-generation companies like CloudCheckr and Alcide. In addition, there are managed security service providers (MSSPs) to which organizations can outsource end-to-end responsibility for cloud security.
Containing Cloud Costs
The frictionless ease with which compute, storage, and other resources can be provisioned and scaled is one of the public cloud’s greatest advantages. Cloud-based agile DevOps has been shown to dramatically accelerate time to market for business-critical apps and workflows, as well as allow them to evolve continuously to meet changing business needs. It is also easy to scale and optimize runtime performance, even in the face of volatile demand.
However, these very same characteristics also make it difficult to monitor and contain cloud costs. For example, resources that were provisioned for temporary purposes, such as testing or staging, may not be decommissioned when the task has been completed; or resources are overprovisioned up front in order to meet peak demand, incurring costs even when they’re not in use. In the RightScale 2019 State of the Cloud report, respondents estimated a 27% wasted cloud spend in 2019, while RightScale (Flexera) has measured actual waste among its customers at 35%. And according to Gartner, by next year (2020), organizations that do not implement effective cost-optimization processes will, on average, overspend in the public cloud by 40%.
There are a number of best practices for containing cloud costs, including:
- Establishing a central cloud team with the skills, technology, and clout to manage and optimize cloud costs, including setting policies and building templates for cloud use.
- Orchestration and automation of cloud resource right-sizing, provisioning, and decommissioning across hybrid and multi-cloud deployments.
- Taking advantage of cloud provider discounts for workflows where demand is relatively predictable and stable. These discounts include different levels of prepayment, as well as Reserved Instances.
- Using less expensive storage tiers for low-latency datasets such as backups and archives.
- Taking advantage of advanced cloud architectures, such as containers, microservices, and serverless (Functions as a Service, or FaaS), which are inherently more efficient in terms of cloud costs. The ephemeral nature of containers, for example, ensures that unused resources get closed down quickly. The pay-per-execution model for FaaS ensures that you aren’t paying for infrastructure resources that you don’t need at the moment.
As with cloud security, the cloud providers and their partners provide a wide range of cloud management tools and platforms that can help monitor and contain cloud costs by providing full visibility into who is consuming cloud services, what the costs are, and whether corporate spend policies are being upheld. AWS, for example, provides a full-featured Management Console, and companies like RightScale (now Flexera) and Scalr offer enterprise-grade cloud management platforms.
Conclusion
Security and cost continue to top the list of concerns that companies of all sizes have as they shift their activities to the public cloud. Acknowledging that these concerns must be addressed effectively, the cloud service providers and their partners offer a wide range of platforms and services for enhancing security and managing costs. The bottom line is that the benefits of the public cloud far outweigh the cost and security concerns—as long as organizations understand their cloud responsibilities clearly and deploy best practices and next-generation technologies diligently.
Reach out to a Media Temple cloud architect to talk more about how we can help you address your security and cloud costs, today.