Why the CIA Trusts AWS Security ... and Why You Should Consider It, Too
In 2013, the CIA signed a huge 10-year deal with Amazon Web Services (AWS) for cloud services. “If one of the world’s largest foreign intelligence services trusted AWS, then your regional enterprise could probably trust it, too.”
In short, if you are one of the 94% of companies that has deployments on the public cloud, keeping those data assets secure is business critical. The good news for AWS customers, however, is that robust security is easily within reach. All your organization has to do is develop a clear cloud security strategy, and then enforce it consistently with the help of the many security services and tools that AWS provides.
Media Temple provides a Managed AWS offering that assists with ensuring cloud security for your AWS implementation, and in this article, we discuss some of the key issues that a cloud security policy should address, and then describe the AWS security building blocks at your disposal.
Cloud Security Fundamentals
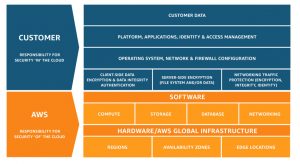
It is important that your company has a clear understanding of what the cloud service provider will secure within the shared responsibility model, and what that means in terms of your company’s security obligations. Although the boundaries of the shared responsibility model will change depending on the service model (IaaS, PaaS, SaaS), AWS is always responsible for securing the infrastructure layer, as shown in the infographic below:
The AWS Shared Responsibility Model, Source: AWS
You can rest assured that AWS invests in and implements the latest in cutting-edge technologies and processes to protect its facilities, hardware, and software from accidental or malicious unauthorized physical or cyber access.
It is up to the customer, however, to protect the apps and data that it deploys and runs in the cloud. In the spirit of “you can’t manage what you can’t measure,” an important first step is to know at all times what assets you have in the cloud, where they are located, and who has (or should have) access to them. Since an organization’s security resources are never infinite, when you categorize assets according to their required level of security controls, you can ensure that security attention and measures are prioritized properly.
Sensitive personal data or data that is subject to compliance requirements must get the utmost protection against loss, corruption, or exfiltration—both in transit and at rest. Did you know that credential theft is the #1 cause of security events? Well, now that you do, you’ll understand that implementing consistent and foolproof access control, together with strong authentication measures, is yet another cloud security fundamental. Proper application of data encryption policies is also really important. Last but certainly not least, effective and continuous monitoring is critical in identifying and mitigating internal and external threats and vulnerabilities as quickly as possible.
Read our blog post, “Don’t Let Cost or Security Slow Down your Cloud Journey“, for additional insights into cloud security concerns and how to mitigate them.
AWS Security Building Blocks
Not only does AWS take extraordinary measures to secure its infrastructures, platforms, and apps, it provides its customers with a comprehensive toolbox for upholding their end of the shared responsibility model. In this section, we’ll overview the AWS security services, categorized into four key areas: access control, monitoring & logging, data encryption, and compliance. Bear in mind that these services are not just to secure your AWS resources. They all have APIs through which you can integrate them into any web-based app or service.
It is also important to note that, no matter how well AWS and you do your security jobs, there is always a chance that a malicious attack, human error, or natural disaster will compromise your data and/or disrupt your business activities. Thus, you must also implement robust backup processes and disaster recovery plans so that you can minimize downtime and maintain business continuity—no matter what. AWS provides a lot of support in those areas as well, but that is the subject of another blog post.
Access Control
- AWS Identity and Access Management (IAM): This is a built-in feature (at no extra charge) of an AWS account. Through IAM, you can create and manage individual and group user accounts, assign permanent or temporary security credentials, and apply role-based permissions to control which AWS resources users or roles can access. One of the really nice things about IAM is that it can integrate with any SAML-compliant identity management solution.
- AWS Directory Service: AWS provides a managed Microsoft Active Directory (AD) service that, among other benefits, lets you seamlessly use AD’s access control features, such as Group Policy and single sign-on, for your AWS accounts. Pricing is an hourly charge per domain-controller hour (with a minimum of two domain controllers per managed directory) plus the number of AWS accounts with which the directory is shared. The base price for the Standard Edition (1GB of storage, ~30,000 objects) is $0.12/hour and $0.018 per additional account.*
- AWS Multi-Factor Authentication (MFA): This is for privileged accounts, with various options for hardware-based authenticators. Virtual MFAs are free, while the cost of hardware devices ranges from ~$13 to $40 per device.*
- AWS Secrets Manager: Remember that credential theft is the #1 cause of security incidents? In April 2018, AWS introduced this service to make it easier to store, distribute, and rotate credentials. The pricing is based on a monthly charge per secret ($0.40) plus a charge per 10,000 API calls ($0.05).*
Data Encryption
Server-side and client-side encryption of data at rest is available in all the AWS storage and database services, such as Amazon EBS, Amazon S3, Amazon S3 Glacier, and Amazon Redshift. AWS also makes encryption available for data in transit using Transport Layer Security (TLS, formerly Secure Sockets Layer, or SSL). And here are the AWS data encryption managed services:
- AWS Key Management Service (KMS): This service gives you a choice between having AWS manage the encryption keys or letting you keep complete control. Your keys are protected with FIPS 140-2 validated hardware security modules. When integrated with AWS CloudTrail (see below), you’ll get logs of all key usage—a great feature for regulatory compliance tracking. With KMS, you pay $1 per month to store each key that you create, while storage is free for AWS managed keys. The first 20,000 requests per month are free, after which you pay $0.03 for every 10,000 requests.*
- AWS CloudHSM: This is an FIPS 140-2 Level 3 validated fully managed hardware security module (HSM) appliance that runs in your own Amazon Virtual Private Cloud (VPC). Supporting all the standard industry APIs, you generate, manage, and use your own encryption keys to which AWS has no access. The price per hour of HSM usage in the US East (Ohio) Region is $1.45.*
- Amazon Simple Queue Service (SQS): This fully managed message queue service was introduced to meet the needs of today’s highly distributed microservice and serverless app architectures. SQS offers server-side encryption (SSE) to encrypt message queues that are transmitting sensitive data. The pricing is on a monthly basis, with the first 1 million requests being free, after which you pay $0.40 per 1 million requests for a Standard Queue and $0.50 for a FIFO Queue.*
Inventory, Monitoring, and Logging
In addition to the wide array of AWS-integrated inventory, monitoring, and logging platforms provided by members of the Amazon Partner Network (APN), AWS offers the following managed services:
- Amazon Inspector: This service automatically assesses Amazon EC2 instances and apps running on them for vulnerabilities or deviations from common security best practices. For example, Amazon Inspector security assessments will alert you to unintended network accessibility of your EC2 instances. Pricing is per month and volume based, starting at $0.15 per instance-assessment for the first 250 instance-assessments in any given month, and going down to $0.04 when the count exceeds 50,000 in the same month.*
- AWS Config: This service monitors and records your actual AWS resource configurations over time, allowing you to assess to what extent they conform to internal or regulatory guidelines. The logs are also useful for change management and operational troubleshooting. Pricing is based on the number of configuration items recorded ($0.003 each), as well as the number of active AWS Config rules. For example, for the first ten active rules, the charge is $2.00 per rule per Region per month.*
- AWS CloudFormation: In order to build security into your AWS infrastructure resources, no matter who provisions them, CloudFormation lets you create catalogs of preconfigured environments (templates). There is no charge for this service other than the AWS resources consumed while using it.
- AWS CloudTrail: Enabled by default, CloudTrail keeps a rolling 90-day record of management events, such as API calls to launch EC2 instances, and operations performed on resources, such as Amazon S3 objects and Lambda functions. CloudTrail’s searchable event logs provide deep visibility into account activities. Charges apply only if you create a trail through which log files are delivered to a specified Amazon S3 bucket.
- Amazon CloudWatch: This service uses logs, metrics, and events to provide a unified view of performance and resource utilization across all your AWS resources, services, and apps. It can be configured to send alerts when specific events occur or thresholds are exceeded, as well as to take automated troubleshooting and remediation actions. The pricing model is pay-per-use for monitoring metrics and API calls, dashboards, alarms, logs, and events.
Acknowledging the importance of log aggregation for effective system monitoring in general, and security/compliance analysis in particular, AWS also offers a centralized logging solution whose architecture combines a number of AWS services, including AWS CloudTrail and Amazon CloudWatch.
Compliance
AWS knows that compliance is a central issue for many of its customers and invests heavily in maintaining certifications for a wide array of global, regional, and national compliance programs. In addition, AWS’s global infrastructure ensures that data residency requirements can always be upheld. At the time of writing this article (April 2019), AWS offers 61 Availability Zones within 20 geographic Regions, with announced plans for 12 additional Availability Zones and four new Regions. AWS customers have complete control over the Region(s) in which their data is physically located. They can also implement redundant deployments to replicate apps and data across multiple Availability Zones or Regions, adding an extra layer of data protection and high availability.
Another way that AWS supports its clients’ needs for data privacy and security is through its strict policies regarding the disclosure of customer information and exposure of customer data. AWS has also never hesitated to advocate against government agency requests for information and data that it feels are overly general or unnecessarily zealous.
Conclusion
Both the quantity and quality of threats mounted against data assets on the public cloud are growing constantly. Whether due to human error, natural disasters, or malicious attacks, no company wants to face the direct and indirect costs of data loss, corruption, or exfiltration. The good news is that data in the cloud can benefit from a very high level of security as long as the data owner or processor makes security a corporate priority, builds a knowledge base of cloud security fundamentals and best practices, and chains together state-of-the-art security services and tools into a robust cloud security stack.
In this article, we reviewed many of the cloud security services that AWS provides its customers, such as access control, data encryption, monitoring & logging, and compliance. In addition, the global AWS Partner Network (APN) program offers a rich array of security solutions, security engineering consultants, and fully managed security services that are tightly integrated with and complement AWS’s security services.
Learn more about how Media Temple can help you migrate to the cloud and implement the security building blocks you need.